


June 5, 2017 Ankur Gupta Business ,
Mobile devices have become the primary medium for accessing content & services now-a-days. Organizations across the globe are developing mobile applications for new customers and for their employees to increase productivity by making enterprise applications.
As per Gartner, by 2017 mobile app development will generate more than $77 billion dollar revenue. This has led to a major concern of data and application security for enterprise businesses, especially businesses that have a BYOD (bring your own device) policy for their users.
This blog focuses on mobile device and application security and some of the major vulnerabilities and commonly used methods for prevention. Furthermore to discuss the need for customers to have a clearly defined security and risk framework that can be used in the development of secure applications by integrating security very early into the software development life cycle.
Security threats are in large numbers now-a-days which can affect mobile devices. These mobile threats can target mobile apps, device, network, data center or any combination of these.
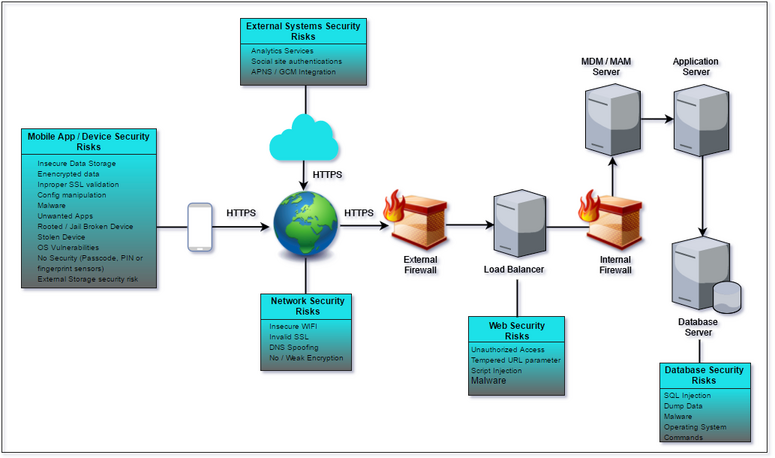
Mobile application faces security threats due to vulnerabilities found in source code. These vulnerabilities can be the result of poor coding standard or lack of security awareness. The following is a list of mobile application vulnerabilities–
User should be authenticated before accessing data, mobile devices come with many authentication options –
But user bypass these security options unintentionally which causes data loss.
Unencrypted data transmissions over the network are a major vulnerability. Few examples are given below-
This makes it easy for the data to be stolen or intercept.
Unnecessary downloads harms devices because it may have malware. It is difficult to identify the difference between a legitimate application and a malware.
Over the last few years major security vulnerabilities have been found in operating systems like iOS, Android.
Users may have done unauthorized modifications to devices. It could increase data security risks.
There is a huge security risk to the organizations associated with stolen employee devices as well.
Mobile app data security threats can be mitigated with the correct implementation of Mobile device management (MDM) & Mobile application management (MAM) tools, following is a sample of some of the controls provided by MDM& MAM tools.
Mobile applications provide convenience to the users and also come up with a number of security risks as user’s personal information such as credit card, internet banking, passwords and more transfers between mobile devices and backend systems across the network.
From an application which does not follow security guidelines can result into user data stolen. For Example: usernames, passwords, authentication tokens, etc.
Encryption systems are upgrading continuously because they are constantly being broken. Apps that allow the data transmission of unencrypted or weakly data are vulnerable.
Mobile applications and the backend systems are connected with best practices of authorization and authentication. This ensures that un-authorized access are identified and blocked.
Mobile applications are designed to exchange data in client-server architecture. If the implementation of source code in mobile applications not secured, unauthorized then hackers can use techniques to see sensitive information while it’s traveling across the network.
If source coded not implemented correctly in mobile application then, hackers can inject text-based attacks that target data and mobile application itself.
Permissions of the mobile apps should be granted wisely because unwanted permission also allows hackers to attack on mobile applications.
In mobile application development we can achieve security risks mitigation with strong& well-formed solutions. The following list shows most commonly used measures of data and mobile application protection from a variety attack methods:
Mobile application and its data security is based on device platform, web-services, cloud-based 3rd party services, etc., Organization should do a detailed analysis of risks against all possible known security threats for mobile applications and use findings to form a secure strategy. This should be used in the early stages of the software development life cycles of the mobile applications. This will result into trustworthy enterprise mobility solutions building with customers.


Hello, I am Aria!
Would you like to know anything in particular? I am happy to assist you.